Are You Data Rich
but Intelligence Starved?
What if you had a SUPER SECURE Data Bridge that strips personal sensitive data from Electronic Health Records?
Introducing 3PSecure Privacy Enabling Technology
Beyond Intrusion Detection
Beyond Firewalls
Beyond Encryption Alone

Finally, Data Security Gets Personal.
Even if breached, sensitive data you own has ZERO Value to BAD ACTORS.
TOKENIZE
MASK
REDACT
data that can be Used by Owner or their Permitted Users to reidentify record
parts of data with value to Fraudsters while still leaving sufficient data for Clinicians, CROs & AI firms to do their job
data that holds no value to Clinicians, CROs, or AI Providers but is extremely easy for Fraudsters to monetize
example:
Patient First Name & Last Name
example:
Month & Date of Birth but not Year
example:
Patient Social Security #
Bad Actors See:
nxtyZ2mnx7 q87zd0kq45
Bad Actors See:
**/**/1982
Bad Actors See:
[blank field]
They NEVER See:
Carla Perez
They NEVER See:
03/06/1982
They NEVER See:
123 45 6789
Genuine Data remains secure in a Remote Token Vault, NEVER Out in the Ether
Finally... Data Security gets Personal
Even if breached, sensitive data you own has ZERO Value to BAD ACTORS
Bad Actors See:
nxtyZ2mnx7 q87zd0kq45
They NEVER See:
Carla Perez
Bad Actors See:
[blank field]
They NEVER See:
123 45 6789
Bad Actors See:
**/**/1982
They NEVER See:
03/06/1982
Genuine Data remains secure in a Remote Token Vault, NEVER Out in the Ether
data that can be Re-identified by
Data Owner or their Permitted Users to reassociate health record
example:
Patient First Name
Patient Last Name
data that holds no value to Clinicians, CROs, or AI Providers but is extremely
easy for Fraudsters to monetize
example:
Patient Social Security #
MASK
parts of data with value to Fraudsters while still leaving sufficient data for Clinicians,
CROs or AI firms to do their job
example:
Month & Date of Birth
but not Birth Year
4 Easy Steps to Infinite Possibilities
PROVISION
Ingest Patient EHRs in
any standard data format
example:
Databases
.CSV files
.XML files
EDIs or APIs
SHARE
Securely Output EHRs in
any standard data format
share with:
AI firms
CROs
Trials, Life Science,
Genetics, etc.
CONFIGURE
Identify Data Fields requiring
De-Identification before Sharing
Tokenize, Mask or Redact fields to obstruct Bad Actors
Configure Roles & Permissions required to re-identify record
ANALYZE
Employ Advanced Knowledge Graph AI provided by Elev8Data or any AI provider
mitigate:
Medical Malpractice
Defensive Medicine
Inform:
Precision Medicine
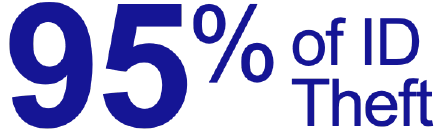
Why Now? A Majority of ID Theft Comes from EHR Breaches


cost of just one data breach
at Change Healthcare
originates from patient health records
in the United States
Don't Let it Happen to Your Organization

Tokenization is an effective strategy for securing credit cards;
it's a natural progression to use it to protect PII & EHR.
Elev8Data's technology is critical to preserve PHI data privacy and security and promote interoperability, which will result in a higher quality of care at lower cost.


Avivah Litan
VP, Distinguished Analyst

Dr. Christ Pavlatos MD
CEO; Orthopedic Surgeon
Where Would You Like to Take Your Data Today?

Secure EHR Sharing
Consistent Compliance with HIPAA-18 &
21st Century Cures Act

Deep AI
for Clinicians
& Business Processes

Superior Care & Lower Cost
for 20% of Population
that account for 80%
of Healthcare Costs

Actuarial Tools
to Identify Candidates
for Precision Medicine

Achieve Your Company's
Top 5 Objectives

Ensuring PHI from
being seen by
Offshore Engineers
Introducing Elev8InsightsAI
Precision Medicine
Ignite the Power of Evidence-Based
NLP Knowledge Graph AI
Proven to:
Extend & Improve Quality of Life
Reduce Cost of Healthcare by up to 50%
Reduce Hospitalizations by 20-50%
Reduce Emergency Visits by 33%
Avoid invasive procedures yet achieve identical outcomes
Employ Optimal Medical Therapy (OMT) to preempt the emergence of serious cardiac & metabolic chronic diseases
Medical Malpractice
Employ Actionable Insights on Local Standards of Care to Mitigate the Risk & Reduce the Expense of Defensive Medicine
Leverage AI to:
Virtually Eliminate the Cost of Defensive Medicine
Identify Safe Harbor Standards of Care by region
Generate Success Metrics to raise HEDIS scores
Identify Failure Metrics with Corrective Actions
Create a Culture of Continuous Improvement
Partners


